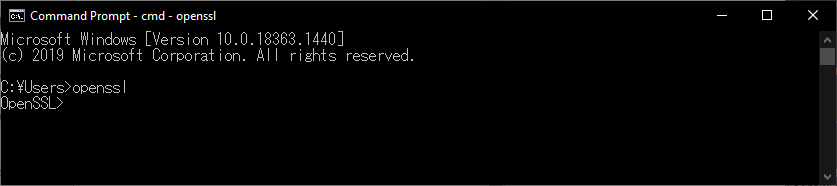
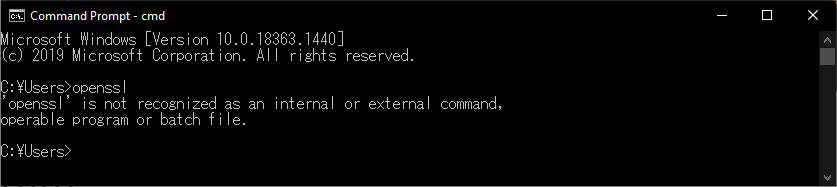
We’ve all been here before. We installed some application e.g. OpenSSL and you want to start the application in a directory other than where the OpenSSL executable is actually located. Bam! Error. You can resolve this by adding the folder where the executable is located to the PATH environment variable.
PATH
PATH is an environment variable on Unix-like operating systems, DOS, OS/2, and Microsoft Windows, specifying a set of directories where executable programs are located. In general, each executing process or user session has its own PATH setting.
Wikipedia – PATH (variable)
Well, that’s still not very clear on what it does. Basically, a PATH is a variable that can be set to directories in which executable programs are located so that it can be started without specifying the entire path to the file. This will work in the Command Prompt (cmd) and in the Run dialog in the Start Menu.
To do this you will have to go to the Environment Variables dialog to add new directories to the PATH variable. You can open Control Panel > System > Advanced > Environment Variables or I prefer the more simple method of running the following command in the Run dialog:
%windir%\System32\rundll32.exe sysdm.cpl,EditEnvironmentVariablesSelect the PATH variable in the User variables list and click on Edit…
Click on New and add the directory path of where the executable is located. We will use OpenSSL as an example.
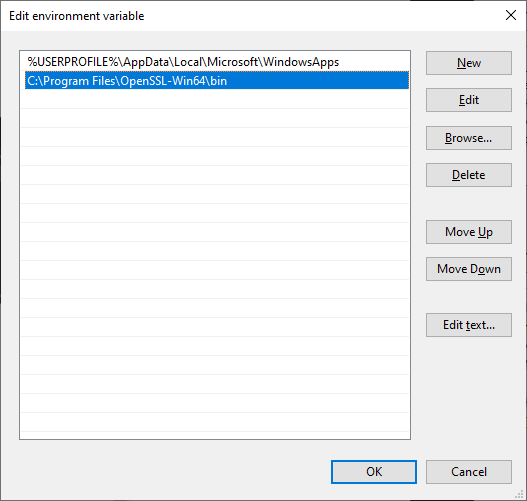
Click on OK to finish.
And we’re done! You’ve successfully added the OpenSSL bin directory, where the OpenSSL executable is located, to the Path variable. Now we can start OpenSSL from the Command Prompt or the Run dialog without specifying the directory path.